Compliant medical record retrieval is a regulatory risk point for every law firm handling protected health information. Incomplete authorizations, unsecured transfers, or missing audit trails can trigger HIPAA violations and stall case preparation.
Legal operations teams need retrieval systems that maintain full compliance while improving speed, ensuring every record request is defensible, traceable, and audit-ready.
This practical guide outlines the regulatory foundations, risk areas, and step-by-step workflows that make medical record retrieval faster, compliant, and entirely defensible across jurisdictions.
Legal and Regulatory Foundations of Medical Record Retrieval Compliance
Understanding the legal and regulatory compliance foundations of medical record retrieval helps firms work more confidently.
HIPAA and Its Core Principles
The Health Insurance Portability and Accountability Act of 1996 sets national standards for protecting patient health information. It regulates how medical data is accessed, shared, and stored, ensuring privacy and security during every stage of record retrieval and case preparation.
In medical record retrieval, HIPAA compliance is guided by three core rules:
- The Privacy Rule governs disclosure of protected health information (PHI);
- The Security Rule defines technical safeguards for electronic PHI; and
- The Enforcement Rule establishes penalties for violations.
Key provisions include the individual right of access (45 C.F.R. § 164.524), the minimum-necessary standard, and explicit authorization requirements for disclosure.
The HITECH Act and Extensions & Enforcement
The Health Information Technology for Economic and Clinical Health Act of 2009 strengthened HIPAA by expanding data privacy and security obligations for all entities handling PHI. It was designed to promote electronic health-record adoption while holding business associates, including law firms and vendors, accountable for maintaining HIPAA-level safeguards.
HITECH introduced direct business-associate liability for downstream handlers of protected health information (PHI), expanding the Office for Civil Rights’ (OCR) enforcement authority to include legal and technology partners. It also strengthened HIPAA’s Enforcement Rule, allowing OCR to impose penalties of more than $2 million per violation category for willful neglect or repeated noncompliance. For legal operations teams, these updates extend compliance obligations to retrieval vendors and the technology systems that manage PHI.
HITECH created direct business associate liability for downstream handlers of PHI, expanding OCR's enforcement exposure for firms and vendors.
Breach notification requirements mandate immediate incident reporting when unauthorized PHI disclosure occurs. When retrieval involves vendors or tech platforms handling PHI, these HITECH provisions create direct compliance obligations for legal operations teams.
Technology and Vendor Compliance
Legal operations teams must evaluate vendor relationships as business associate arrangements requiring comprehensive Business Associate Agreements. These agreements establish shared accountability for how PHI is handled throughout the retrieval process.
Technology platforms used in record retrieval also fall under HIPAA’s Security Rule, which mandates administrative, physical, and technical safeguards—most notably access controls, encryption standards, and detailed audit logging.
Applying these safeguards ensures that every data transfer, storage event, and user action can be verified through defensible audit trails and documented compliance.
Additional State-Level Considerations
State laws often impose stricter requirements than federal HIPAA minimums. Timeline requirements vary dramatically, for example.
- Washington requires medical practitioners to make records available within 15 days.
- California mandates 5 working days for viewing and 15 days for copies.
Jurisdiction mapping needs to consider provider location, patient residence, and requester location, and legal operations must comply with the most restrictive applicable standard.
Key Compliance Risks in Medical Record Retrieval
Due to strict regulations, retrieval compliance errors can lead to liability exposure for medical malpractice and personal injury law firms. The most common risk areas include:
- Missing or invalid authorizations are the primary source of HIPAA violations. Authorizations must meet both state and federal standards across scope, purpose, and signature. Non-compliance leads to retrieval rejections.
- Over-disclosure of PHI: The minimum-necessary rule requires limiting disclosures to information directly relevant to the case. Excess data release increases breach risk and regulatory exposure.
- Insecure transmission or storage exposes firms to regulatory penalties and cyber-liability risk. HIPAA standards require encryption for all electronic PHI and a verified chain of custody for physical records. Failure to secure data compromises compliance and defensibility.
- Weak audit trails reduce defensibility during investigations. The HIPAA Security Rule requires complete logging of PHI access and disclosures to demonstrate compliance with OCR audit standards. Missing or incomplete records jeopardize regulatory standing.
- Multi-state regulatory variation introduces conflicts in timelines, formats, and fee requirements. Firms operating across jurisdictions must apply the most restrictive standard to maintain consistent compliance and avoid procedural violations.
- Vendor and technology oversight failures create direct business-associate liability. Regular audits, executed Business Associate Agreements, and monitored incident-response protocols are necessary to uphold compliance and minimize enforcement risk.
How To Create a Compliant Medical Record Retrieval Process
A compliant retrieval process follows a clear sequence, from defining scope to final delivery, ensuring every stage meets HIPAA and state-specific requirements.
1. Define the Retrieval Scope
Start by identifying which records, providers, and time periods are relevant to the case, and document the legal basis for accessing PHI. Determine the governing regulations: HIPAA, state privacy laws, and jurisdictional rules, and, in multi-state matters, apply the most restrictive standard.
Depending on firm structure, retrieval may be handled internally or through third-party partners operating under Business Associate Agreements that ensure HIPAA compliance.
2. Establish Retrieval Requirements
Prepare valid authorization forms that meet both HIPAA and state-specific requirements, including signatures, defined scope, stated purpose, and expiration terms. Some states add language, notarization, or witness requirements, making jurisdiction-specific templates essential.
When records are requested directly by patients, apply HIPAA’s right of access, which carries distinct authorization and fee structures from those used in legal proceedings.
3. Make Sure Submission and Retrieval Is Secure
Transmit requests through secure, trackable channels that log receipt confirmations and provider responses.
Encrypted electronic submissions reduce turnaround times and allow automated status monitoring. Standardized forms, including patient identification, record scope, authorization, and delivery details, minimize provider rejections.
For retrievals managed by external vendors, maintain HIPAA compliance through executed Business Associate Agreements and secure-portal integrations that limit manual handling of PHI.
4. Review & Verify
Once records are received, review them for completeness and verify that all documents match the original request.
- Identify gaps or missing time periods before filtering for relevance.
- Apply the HIPAA minimum-necessary rule to limit disclosure to case-related information, using role-based permissions to maintain appropriate access control.
- Preserve the chain of custody with metadata logs and version control.
Electronic files require integrity checks, while scanned physical documents must retain an auditable trail.
5. Retention, Audit & Compliance Review
Store authorization forms, medical summaries, retrieval logs, and audit trails in accordance with legal and regulatory retention timelines.
- Maintain data integrity and continuous access logging within secure electronic repositories.
- Conduct regular audits to assess timeliness, completeness, and vendor performance.
- Use documented incident-response protocols to address PHI breaches or disclosure violations, reinforcing compliance and broader risk-management standards.
How Does Automation Improve Medical Record Retrieval Compliance?
Automated medical record retrieval reduces delays and increases tracking visibility. As a firm’s case load increases, AI-powered legal tools can minimize scale-related errors and keep staff allocated to strategic work. Via automation, legal teams enjoy:
- Case-management integration to manage retrieval requests within existing case systems through automated submission, vendor coordination, and real-time status updates, reducing manual workload and missed deadlines.
- Secure provider portals for direct provider uploads into firm-designated repositories, minimizing PHI handling, reducing transcription risk, and preserving audit trails.
- Access controls aligned with minimum-necessary standards, with detailed activity logs that support compliance and evidentiary review.
- Digital authorization workflows that generate HIPAA-aligned forms automatically, validate required elements before submission, and reduce provider rejections while improving turnaround times.
With automation, record retrieval drops from weeks-long processes to days, while maintaining HIPAA compliance and measurable oversight.
Building Sustainable Medical Record Retrieval Compliance Operations
Building a compliant medical record retrieval process is essential to both case success and firm protection. Achieving speed and defensibility requires clear regulatory foundations, well-defined workflows, automated controls, and measurable metrics that make compliance sustainable over time.
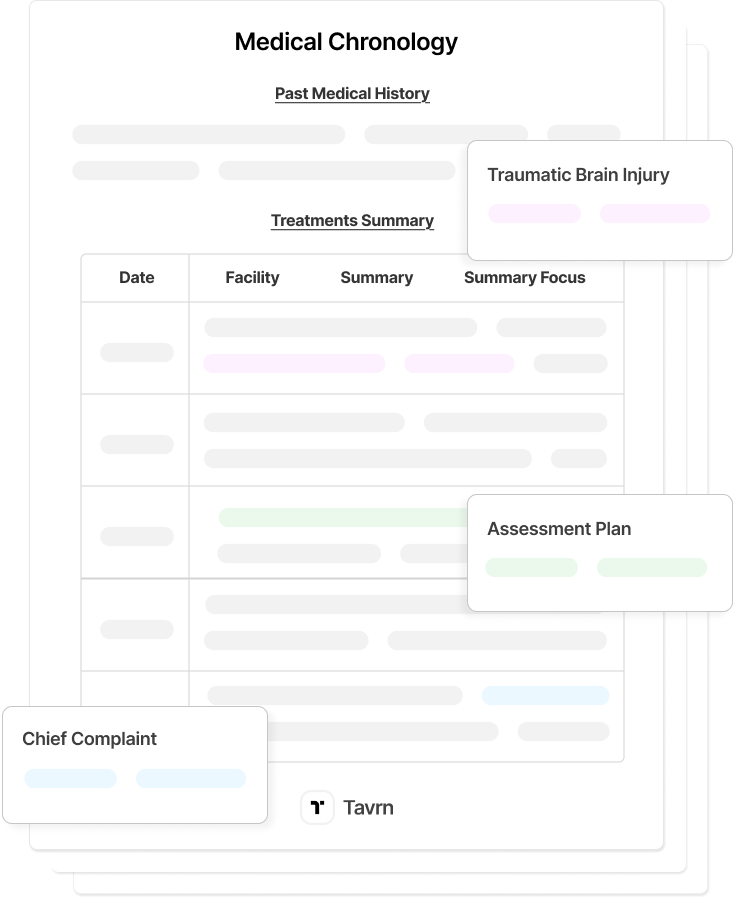
Tavrn’s medical record retrieval platform is designed to implement retrieval workflows, secure portals, and audit-ready controls that align with professional responsibility standards and investment validation.

































.webp)
.webp)